- Private key: This key must be known only by its owner.
- Public key:This key is known to everyone (it is public).
- Relation between both keys: What one key encrypts, the other one decrypts, and vice versa. It means that if A encrypts something with B’s public key (which A would know, because it's public), B would need his private key to decrypt the message.
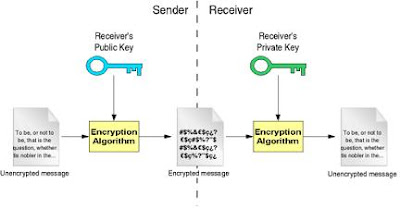
In a basic secure conversation using public-key cryptography, the sender encrypts the message using the receiver's public key. The encrypted message is sent to the receiving end, who will decrypt the message with his private key. Only the receiver can decrypt the message because no one else has the private key. Also, the encryption algorithm is the same at both ends: what is encrypted with one key is decrypted with the other key using the same algorithm.
Key-pair Generation:
A public key cryptosystem is based on a “trap door one-way function,” that is, a function that is easy to compute in one direction and hard to compute in other direction. The purpose of the trap door is to ensure that an attacker cannot use the public information to recover the secret information.
 Figure 5. Public key generation
Figure 5. Public key generation