
Figure 3. Key-based Symmetric algorithm
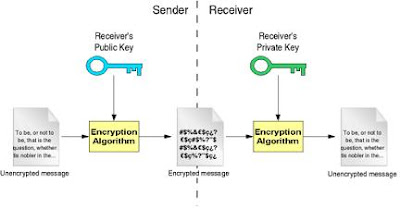
Asymmetric key-based algorithm uses two keys - the key used to encrypt a message differs from the key used to decrypt it. In this, a user has a pair of cryptographic keys — a public key and a private key. The private key is kept secret, while the public key may be widely distributed. Messages are encrypted with the recipient's public key and can only be decrypted with the corresponding private key. The keys are related mathematically, but the private key cannot be feasibly (i.e., in actual or projected practice) derived from the public key.
Figure 4. Key-based asymmetric algorithm




Excellent blog. You have explained the complete concept of symmetric and asymmetric key based algorithm in a very simple way. The diagrams posted above gave a clear overview of both the terms. Thanks for writing in such a good way.
ReplyDeletedigital signatures